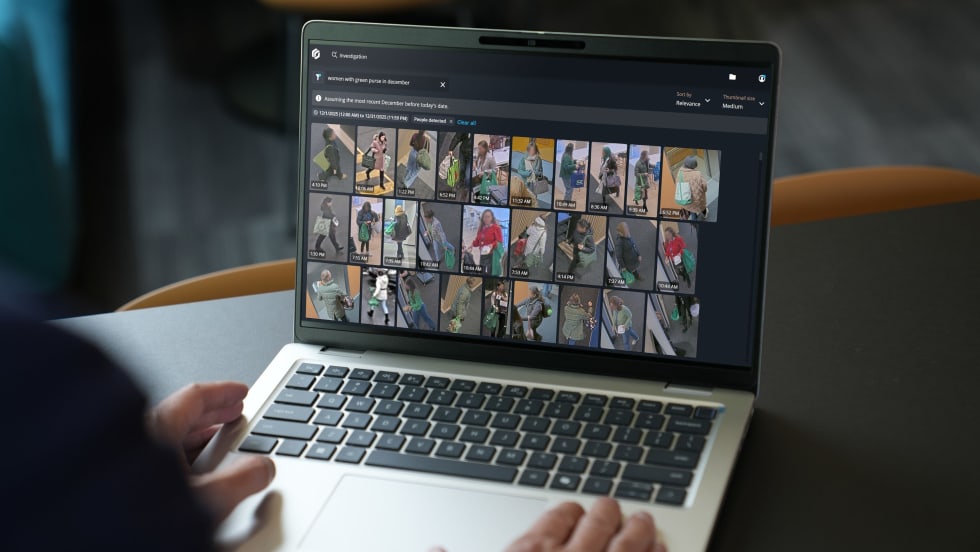
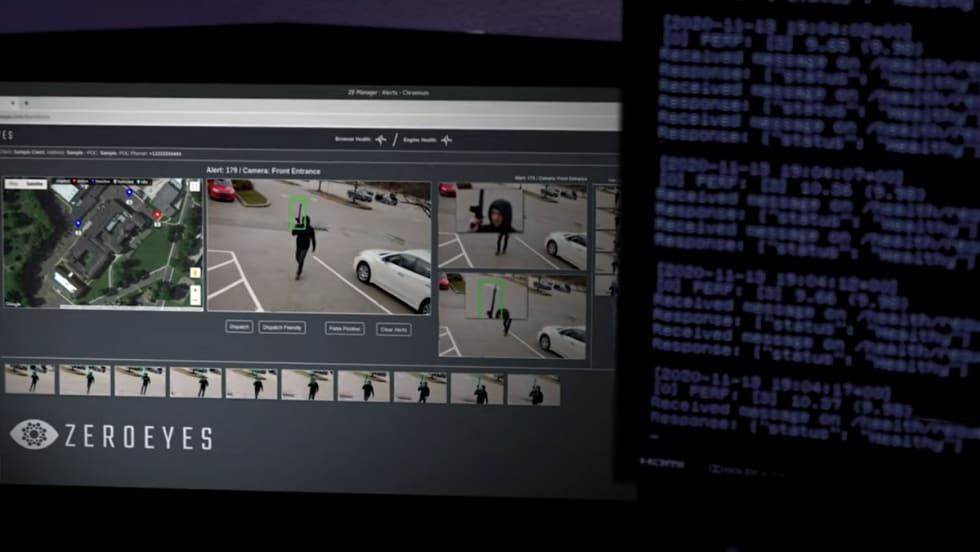
Computer criminals can be anywhere in the world, but the victims are here, so American law enforcement has to investigate and respond. Unfortunately, most agencies don't have the tools or know-how to do so.
In the movies and on TV shows people who commit computer crimes are often depicted as masterminds. They are geniuses with amazing programming skills who take down multinational corporations for millions and even billions of dollars. But the truth is that crimes committed over computers are often perpetrated by people with nominal digital skills and the targets are more likely to be your average American than some nameless, faceless corporation. That means victims of cybercrimes can and do report them to local law enforcement. Unfortunately, few American law enforcement agencies are equipped to respond or investigate.
Cybercrimes are often perpetrated anonymously and the perp could be literally anywhere in the world, so what can local law enforcement do about them?
Before we explore the answers to that question, and there are many different answers, it's important to get a handle on just what constitutes a cybercrime. In 2013, the Police Executive Research Forum (PERF) crafted a fairly comprehensive definition of "cybercrime" for a survey. According to PERF, cybercrime is a range of crimes, including theft or fraud; hacking, data/identity theft, and virus dissemination; or the storage of illegal material such as child pornography in digital form. The only thing all these crimes have in common is that they can be perpetrated using a computer. Where this definition fails is that just about every criminal act today involves a computer. The guy selling heroin may use a smartphone (otherwise known as a handheld computer), e-mails may establish the association between the members of a burglary ring, and a murderer or rapist may have kept images of his target on a tablet.
In order for local law enforcement agencies to combat cybercrime, they need to know what resources are available. Many agencies turn first to the feds, and rightfully so. The FBI and the United States Secret Service are the agencies best equipped to investigate cybercrime, and they have worldwide reach. The problem is the feds can't handle every cybercrime case and certainly not every criminal case with a cyber element. Which means local law enforcement agencies have to shoulder much of the burden.
Whether a law enforcement agency is equipped to perform a digital investigation comes down to the skills and training of its officers and the tools available to them. But most agencies do not have this capability. Which is one of the reasons why the closure rate on cybercrime cases is abysmally low.
Combining Resources
The first thing local agencies need to do about cybercrime is encourage victims to report the crime. There are a variety of reasons why victims are often reluctant to report cybercrimes. But it basically comes down to one or all three of the following: the amount of money involved is too small to worry about; they don't believe anything can be done about it, and/or they don't know where they can report such crimes. The FBI has set up the Internet Crime Complaint Center (IC3.gov) so that cybercrime victims have a place to turn. Of course, they can also report these crimes to local law enforcement agencies. Unfortunately, very few officers who respond to such complaints know what to do about them.
What happens after such a local complaint depends on the agency. Some agencies have cybercrime investigators and digital forensics specialists, but many don't have the personnel, money, or expertise to pursue such cases. Experts recommend that agencies pool their resources in task forces and regional cybercrime teams. "Combating cybercrime is a team sport," FBI Assistant Director Joe Demarest said at a 2014 PERF conference on cybercrime. "Whether it is a local, state, or federal level agency, one agency can't do this alone."
A number of cybercrime investigative teams and task forces have been set up across the country. The Secret Service (SecretService.gov) has organized 37 Electronic Crimes Task Forces (ECTF) in the United States and two overseas in London and Rome. The ECTFs were created in the 2001 USA PATRIOT Act and have the mission of preventing, detecting, and investigating cybercrime. Task force participants include law enforcement agencies at all levels and private companies that are often the target of cybercrimes.
To give local agencies access to digital forensics expertise, the FBI operates 15 Regional Computer Forensics Laboratories (RCFL) nationwide and is planning to open two more. An RCFL (RCFL.gov) is both a digital forensics lab and a training center. It provides support for criminal investigations involving digital data.
Digital Investigators
There are two schools of thought regarding the officers who conduct cybercrime investigations. Some experts say the digital skills are most critical. Others say detectives can be trained to do the job. "I can teach a good detective how to investigate computer crime much faster than I can teach a computer guy to be a good detective," Slomo Koenig, a detective with the Rockland County (NY) Sheriff's Office said in a 2003 POLICE Magazine article ("How to Investigate Cybercrime," November 2003).
Of course someone can't be computer illiterate and be a cybercrime investigator. Becoming a cyber sleuth requires skill as a detective and training in how computers are used in crimes and how evidence of these crimes can be collected from computers.
Finding officers with the skills to be a cyber investigator is difficult. But the Toronto Police Service has taken great pains to do so. "One of our HR strategies is to catalog all the talents that our recruits bring to the organization," Toronto Deputy Chief Mike Federico said at the 2014 PERF cybercrime conference. "When they graduate from the police academy, we take a close look at their background information. I would recommend that all departments keep an eye out for talented people in their graduating classes."
Searching for talent within their own agency led Toronto Police management to find a civilian employee in the parking division who was a computer and social media expert. Deputy Chief Peter Sloly told the PERF conference that the man has been "involved in solving some of our most high-profile cases."
Recently, the Pottawattamie County (IA) Sheriff's Office found a talented cyber investigator in the ranks of its reserve volunteers. The reserve was the county's former IT manager, Tony Cava, and he helped close a baffling 2012 murder.
That case involved the disappearance of a woman named Cari Farver. Although no one knew her whereabouts, her family and friends continued to receive texts and e-mails, and Farver's social media accounts remained active. Kava's cyber skills helped the detectives gather evidence that Shanna Golyar was digitally impersonating Farver. Golyar was convicted of murdering Farver in 2016. Her motive was reportedly jealousy over a boyfriend.
Kava told KETV that unraveling Golyar's digital web of deceit was a massive undertaking. He donated 3,000 hours of work to the case and developed his own software programs to help him manage all the evidence, including 60 different e-mail accounts that Golyar was using to impersonate her victim. "It was really mapping out a network and at the center of it you had the suspect," Kava explained to the TV station.
Kava is now the Pottawattamie County SO's first cyber investigator. Sheriff Jeff Danker told KETV that the rise of cybercrimes and crimes with cyber elements like the Farver murder led him to hire Kava. "You need someone to sort through this and put the case together," he said. "It's not typical for an investigator to be trained in and have this specialized knowledge. We are fortunate to have Tony in this position."
Finding the Training
Tony Kava brought a wealth of computer and investigatory skills to the investigation of Kari Farver's disappearance. In addition to being a computer IT expert, he had also volunteered with the Iowa Crimes Against Children Task Force. Most local agencies that need to conduct cybercrime investigations do not have a Tony Kava. So they have to hire outside experts who already have the skills or have some of their personnel train to become cyber investigators.
There are a variety of ways that law enforcement officers and civilian personnel at law enforcement agencies can gain the necessary training to become effective cyber investigators. Makers of digital forensic tools and software offer training on their platforms. There are also a number of schools and private trainers that offer cyber investigation training. But perhaps the best option is absolutely free to the agencies that need training for their officers, the National Computer Forensics Institute (NCFI)
Located just outside of Birmingham, AL, the NCFI was established in 2008 with the mission of training and equipping local law enforcement agencies in digital evidence collection and cybercrime investigation. The NCFI says its training is based on the Secret Service's cyber investigation strategies, which focuses on building partnerships with and sharing information between law enforcement, academia, and private industry.
Since its opening in 2008, the NCFI has trained state and local law enforcement, prosecutors from all 50 states and from more than 500 agencies. "The impact that these graduates have made is noteworthy. In the absence of NCFI, the forensics investigations performed by graduates would either not have been conducted or have been forwarded to federal agencies where they may not have received a priority. With NCFI training, the graduate's agency has the capability to conduct their own investigations," says the NCFI
website.
Eligible law enforcement and judicial personnel must submit an application to the NCFI. If accepted the student must train at the training center in Hoover, AL. Cost of travel, lodging, and a per diem are paid by NCFI. Training offered by NCFI includes: network investigation, social media investigation, evidence recovery, mobile device examination, how to detect and respond to hacking, and other critical cyber investigation skills.
A detective from the Bowling Green (KY) Police Department gave the following testimonial about the NCFI. "Prior to this training, my department would have had to wait one to two years to get a computer examined. Now that I have been trained and equipped, we have just a few weeks' turnaround."