Cell phones can provide investigators with a call history, text messages. and contact lists. They can also provide us with other valuable data that's sometimes overlooked.
Read More →
The Department of Justice on Tuesday dropped its support for allowing law enforcement to review older e-mails without a warrant in testimony before the House Judiciary Committee.
Read More →
ATC-NY's new computer forensic tool, Windows Memory Reader, is a simple command-line utility to capture the contents of physical RAM on a suspect computer, letting an investigator gather volatile state information prior to shutting the machine down.
Read More →
The Orange County (Fla.) Sheriff's Office has acknowledged its computer investigator missed evidence of a Google search for "full-proof" suffocation methods on the day Casey Anthony's 2-year-old daughter disappeared.
Read More →
Saelig has introduced a shielded forensic pouch (Model No. SFP1215W) that enables hands-on manipulation of wireless devices in an RF-tight environment so internal data is not compromised.
Read More →
Cellebrite's UFED Touch allows investigators to more easily extract and decode digital evidence from mobile devices including smartphones, legacy phones, portable GPS devices, and handheld tablets.
Read More →
Advances in technology have made it possible for any officer, with minimal training, to retrieve digital evidence at the crime scene and utilize it for investigative purposes.
Read More →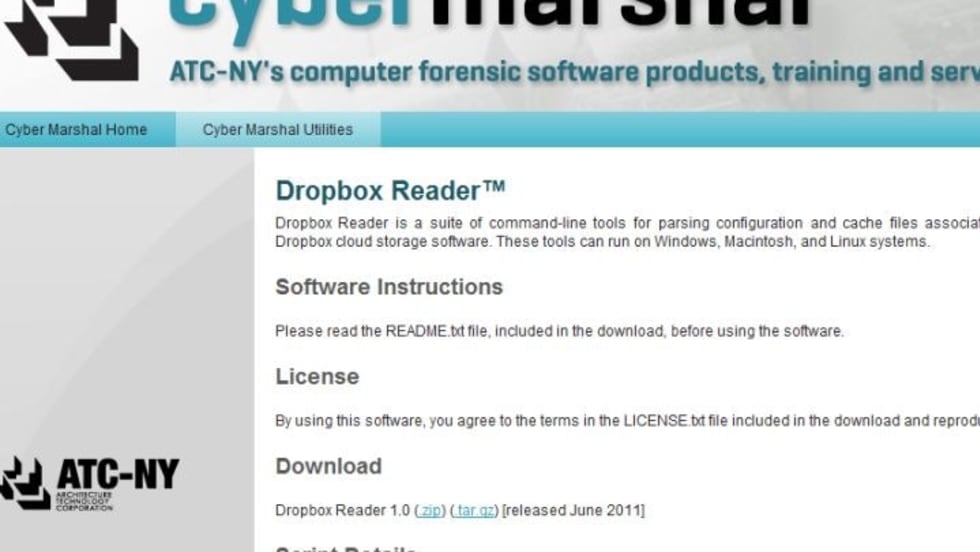
Dropbox Reader, which is used to analyze files on a hard drive, can run on Windows, Macintosh, and Linux systems. With Dropbox Reader, you can acquire information about the registered Dropbox account, shared directories, and synchronized files.
Read More →
EnCase Forensic gives investigators the ability to image a drive and preserve it in a forensic manner using the EnCase evidence file format (LEF or E01), a digital evidence container vetted by courts worldwide. EnCase Forensic also contains a full suite of analysis, bookmarking, and reporting features.
Read More →The new solution lets officers in the field quickly and securely identify evidence on a wide variety of digital devices, including Windows, Linux, and Macintosh computers, and cell phones. The system also reads memory cards.
Read More →