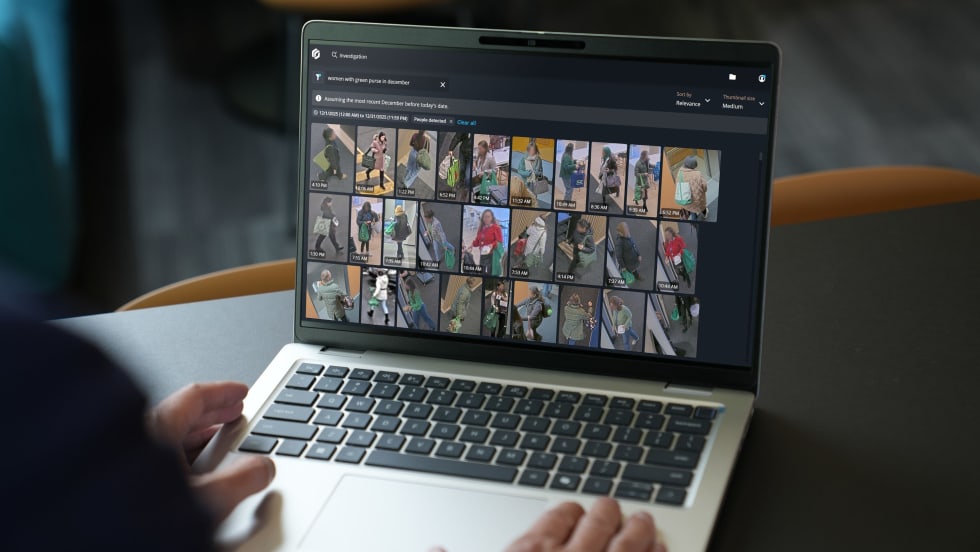
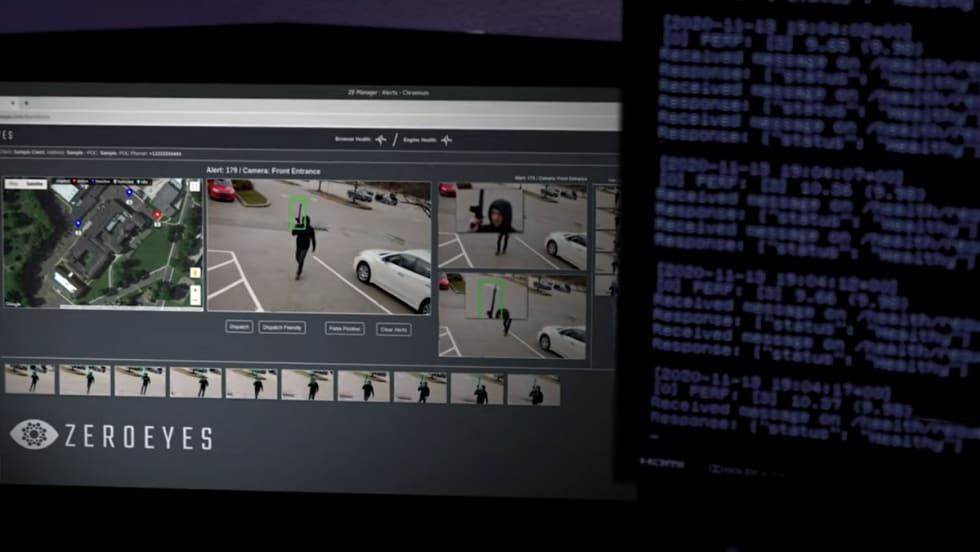
Some people will attack your network for money, some for ideology, and you don’t want make it easy for them.
We are certainly living in “interesting times,” which is nice way of saying things are not necessarily good nor bad, just “interesting.” The physical and political threats to law enforcement and law enforcement officers are obvious and have been discussed by others in detail. I would like to discuss other threats: cyber attack and data exfiltration.
Simply defined, a cyber attack is any kind of malicious activity that attempts to collect, disrupt, deny, degrade, or destroy information system resources or the information itself. It is important to realize that a cyber attacker has a goal they want to accomplish.
Currently, most attackers simply want money. While activist cyber attackers exist, they are far outnumbered by attackers simply attempting to make money. There is an entire industry of cyber attackers on the dark web where credentials are traded, data is exchanged, and hacking as a service exists with service level agreements that include not paying if they aren’t’ successful. You can, quite literally, hire someone to attack someone else for you.
Data Held Hostage
Public safety leaders need to realize that their agencies’ data can be a target of “hacktivists”—hackers with a political agenda—not just digital thieves. The method of attack will be similar but with money not being the goal simple data destruction or leaking of information without demands for ransom may be the result.
One of the most successful money-making strategies of cyber attackers is ransomware. Inserting malicious code on your device or network and encrypting your data so you can’t use it. They then hold your data hostage until you pay them to provide the encryption key to decrypt your data or they do it for you. Ransomware has been around for awhile but in the past few years the business model has evolved. Ransomware attacks now do not solely focus on encrypting your data and holding it hostage. The current trend is they exfiltrate your data before encrypting it so they can hold you hostage to decrypt it, hold you hostage again or sell your data, and a third time to prevent them from telling anyone you were compromised.
Data exfiltration is a form of a security breach that occurs when an individual’s or company’s data is copied, transferred, or retrieved from a computer or server without authorization. Essentially, they steal your data.
Public safety agencies and law enforcement possess a tremendous amount of data that is very sensitive in nature. As a profession we are very familiar with the security of things like physical evidence, weapons, ammunition, and facilities. As agencies have adopted digital case files or are migrating to them the amount of sensitive data is rapidly increasing.
Information Security
Having had a rather unique role at my former agency of being responsible for “IT” security, physical security, and information security brought the cyber threat to my attention.
Information security is likely more familiar to some LE folks who have experience in Records Units. It is basically the controls of who is allowed to receive your information. Case files, reports, or other records. Many, many pieces of LE information leave the agencies control every day. Case files, reports, etc. are sent to other agencies, courts, prosecutors, etc. Agencies should have robust policies and procedures regarding who is authorized to receive information and how it is tracked. These are all necessary and a must have for law enforcement, but it isn’t enough. This is all “intended” informational release. Either persons were vetted and allowed access, or a person is allowed to release.
Cyber security for public safety/LE has a huge component in protecting the privacy of the citizens you serve, the privacy of your employees, and the security of your evidence and investigations. A successful cyber attack of a public safety network is an unauthorized person gaining access to your data, and if they exfiltrate it then it is now in their control.
Many agencies are served by municipal IT Departments, and I am certain quite well. There are many agencies that are very small, in small municipalities or units of government with far more limited resources. It has been my experience that far too often there is too large of gap between a public entity’s IT Department and public safety.
The needs for IT security for public safety is larger than for other departments. The FBI CJIS security policy is a good starting point. The controls they demand for access to, the storage of, and the transmission of criminal justice information are excellent controls for all your data and systems.
As law enforcement leaders it is critically necessary to educate yourself on the basics of cyber security and to understand the threat. That way you can ask the right questions of IT to determine if you are mitigating the threat as best as possible. If your IT doesn’t understand law enforcement data and your systems and you don’t understand how they support your operation, then you have a lot of work to do to close the gap between yourselves. Essentially, we need to merge the understanding of informational security and technical cyber security together, so both are on the same page. The one is incomplete without the other.
Best Practices
So how do you protect your data? Some very basic best practices are a good place to start.
Audits—Identify where public safety data is stored and who has access to it. Anyone with access to the data should be vetted and “least access” privileges should be enforced. Just because someone could have access to something doesn’t mean they should have access to it. I doubt many folks in your agency have access to the evidence room. The same principles apply to data. Also, access should be routinely audited to ensure that all offboarded employees no longer have access to your systems and their accounts are shut down regardless of if they could access the network anymore. Old, stale, dead accounts are threats to your data security.
Anti-Data Exfiltration Technology—Analyze and protect the data leaving your network and computers not just what is coming “in.” Traditional approaches to Cybersecurity involve defending the perimeter of your network. This approach doesn’t protect what is leaving your network (your data). Invest in technology that analyzes outbound communications. This stops the theft of your data.
Multi Factor Authentication (MFA)—Access to public safety data and systems should be protected by multi factor authentication. MFA is sometimes referred to as 2 FA (second factor) authentication. This is another form of ID to gain access to data/systems beyond that of a password. There are many different types of these systems. Some are “better” (harder to compromise) than others. App based “push” alerts are better than numeric codes sent to smartphones as SMS (texts) because it is possible to clone a SIM and receive the text as a malicious actor. However, “push” alerts to apps require your user to be diligent in not approving a push they didn’t initiate themselves. Attackers have taken to relying on the human getting tired of receiving repeated push alerts and then just approving the push to stop getting them. Physical tokens are an option but of course harder to keep track of.
Encrypt Your Own Data—If your data at rest is already encrypted, it is better protected. Data stored on endpoints in physically unsecure space (i.e., laptops) should be encrypted by the agency. Laptops with your data on them are just big thumb drives waiting to be stolen or lost. The transmission of the data should be encrypted also. End point to end point encryption via VPN or point to point network encryption should be employed.
Admin Privileges Restricted—End users regardless of rank should not have administrative privileges on law enforcement systems or computers. If a user has admin privileges on a device and it is compromised, then an attacker with their credentials has administrative privileges on the device as well. Those IT personnel with administrative privileges should have secondary accounts with admin privileges rather than their primary accounts having administrative privileges. That means their public facing, day-to-day business account for e-mail, etc. should not have administrative privileges. They should have to use specific accounts for when they need administrative privileges, and those accounts must require 2FA or MFA to secure that access. This is a critical step that not everyone in IT will like. It is more cumbersome and less efficient for them to have to use specific accounts for administrative privileges, but it greatly reduces the risk of their account being compromised.
Network Segmentation—If your network is part of a larger municipal or county network you should be asking your IT Department to segment your portion of the network from the rest. A user on the network from another city or county department should not be able to access your portion of the network period. Network rules can be set that prohibit that from happening. Mostly this is logically separating the networks not physically. Physical segmentation would be ideal but is far more costly. If an attacker compromises a user at City Hall, you need your network to be configured so that they cannot elevate their permissions and transit the network to your law enforcement network. In the private sector this is referred to as “lateral movement.”
Costly Damage
In the private sector, one of the most serious costs of a data breach is loss of reputation. Customers and other companies may be reluctant to do business with another business that suffered a data breach. Especially when they are not forthcoming about the breach. Law enforcement is very aware of the damage to trust and public perception regarding critical incidents. I would ask you if you have considered the damage to reputation or trust if your law enforcement records are compromised. If the PII of crime victims were released into the wild, or if your law enforcement records were destroyed. Do you have a plan for cyber attack response. Law enforcement has unique and additional burdens when it comes to law enforcement data than other city departments may have.
Law enforcement leaders need to be part of the conversation when disaster recovery is being discussed from an IT perspective. Also, IT needs to be planning for more than “smoking crater syndrome” (physical loss of a data center). It needs to be prepared for the destruction or theft of data and what to do next.
I am old enough to remember working in a patrol car with nothing but a radio, a shotgun, and paper forms. Can your organization do that now? What is your plan if everything IT is down? How long can you function? Agencies in this nation have had this happen to them, including PSAPs losing CAD functionality and total loss of networks due to cyberattacks to entire agencies losing any functionality for their systems from RMS access to even email. Have a plan, exercise the plan, be prepared. Most importantly protect the public you serve by protecting the information they have given to you. Some due to legal requirements and some voluntarily so that you can help them.
David Schnurstein is a 25-year veteran of law enforcement. He retired as the Commander of the Emergency Communications, Records & Technology Division for the Grand Rapids (MI) Police Department.