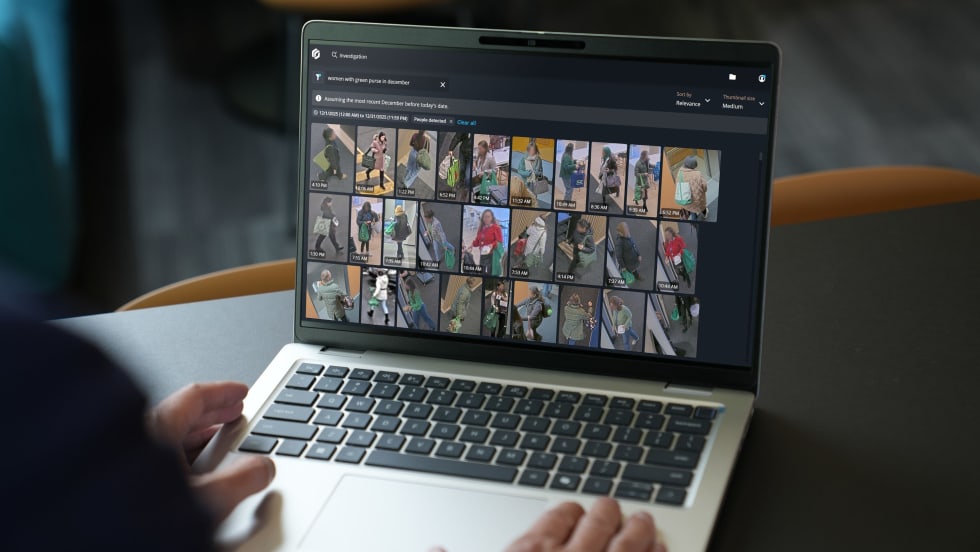
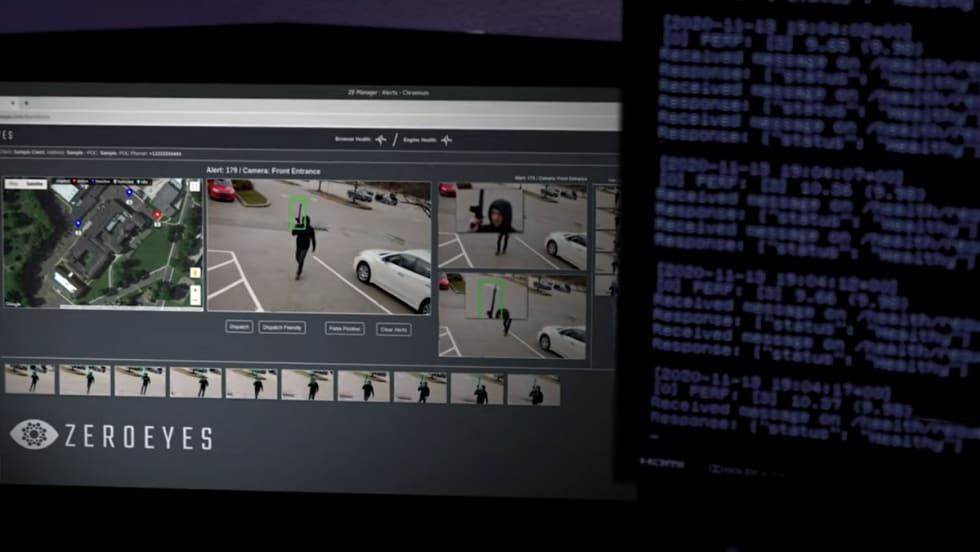
Domestic extremists are an increasing and ongoing threat to public safety. By unmasking their identities and communications, law enforcement can discover plots and prevent attacks.
The United States has experienced disruptive activities from a wide variety of extremist groups and individuals over the past few years. According to a May 2021 report on domestic terrorism that was jointly released by the FBI and Department of Homeland Security (DHS) covering 2017-2019, “2019 represented the most lethal year for Domestic Violent Extremist attacks since 1995.”
In addition, the FBI’s 2019 annual Hate Crime Statistics report (the most current data available) further reflects that there were 7,314 hate crime incidents involving 8,559 offenses of which 7,103 were single-bias incidents. The report categorizes these crimes into six areas. The leading statistic shows that 57.6% of incidents were motivated by race, ethnicity, or ancestry, 20.1% were attacks against a person’s religion and 16.7% were attacks targeting a victim’s sexual orientation. The remaining attacks were against a person’s gender identity, disability, and gender.
When law enforcement officers need to investigate an extremist-caused incident, they are confronted by many case-related challenges, especially when it involves working in the online world. Thanks to the Dark Web (a part of the web only accessible via a specialized browser that employs masked IP addresses, making it easy for users to hide their identities and activities) and other online tools, tech-savvy extremist groups can hide their identities and the events they are discussing or planning online.
The good news: It is possible for law enforcement to hunt extremists on the web, by using advanced deep intelligence tools enabled by artificial intelligence (AI) and machine learning (ML). However, mounting an effective, ongoing response to online extremists requires law enforcement agencies to dedicate full-time officers and resources to the task, just as they already do in areas such as drugs, gangs, and vice.
Know Thy Enemy
To unmask, deter, and apprehend domestic extremists, an investigator needs to know their mindset and likely mode of operations. The reason: Although the motivations driving extremists vary widely, their online behavior and methods often reflect common traits and
patterns.
One word of warning: These days, extremists exist in all ethnic, economic, and geographic groups in the country, and they fit right into everyday life. They look “normal.” So, relying on stereotypes associated with far-left or far-right radicals can be short-sighted and often plain wrong when trying to ferret out domestic extremism.
On the web, extremists live within their own online echo chambers. They prefer to interact only with like-minded people and avoid anyone espousing mainstream beliefs. Extremists also exploit the anonymity of the web—especially the Dark Web—to create multiple online accounts and personas, often portraying themselves as more dangerous and important than their public places in society indicate them to be.
The fact that the web makes it simple to organize activities across vast distances and the ease with which like-minded extremists can congregate in online chat environments, means that coalescing into distinct groups has become common for extremists these days. Add the distinct slang, politically-tinged emojis, and memes, and the ‘dog whistles’ (short, loaded phrases that reference their prejudices) that accompany their online communications, and the online world is a nurturing incubator for extremists and their violent intentions.
Web Warfare
Unfortunately, extremists have many online weapons at their disposal to plot against and actively harass law-abiding members of society – and the police and other agents of authority who work to protect them. This is because the social platforms used by the public for sharing information among family and friends are rich sources of open intelligence for extremists wishing to research, target, and physically attack anyone that they oppose.
One noxious form of attack is called “doxing.” This occurs when an extremist posts the personal contact information of a selected (and often unknowing) adversary online on specific Dark Web sites, to encourage other extremists to harass this person using threatening emails, text messages, robocalls, and posted lies designed to ruin their reputation and demoralize them.
There are many other weapons of web warfare that extremists employ such as “deanonymizing” themselves (often using false identities) to spread disinformation and sow social disruption via mainstream online outlets. They also claw at the social fabric in many ways such as by inserting scenes of violent police responses in other countries to video feeds purporting to be shot within the United States.
These acts of web warfare are funded in a variety of ways. Cryptocurrencies and crowd-sourcing websites make it easy for extremists to attract donations for their causes, no matter how odious they may be. In particular, the anonymity associated with cryptocurrencies allows like-minded donors to effectively shield their views from the general public.
Investigating Extremists
The anonymity provided by the Dark Web - versus the Surface Web that most people use - is the first and most obvious reason that extremists are difficult for law enforcement to investigate. Unlike the Surface Web, the Dark Web cannot be searched by mainstream search engines. If you don’t know the specific IP address of an extremist website, you can’t find it.
In this environment, it can be difficult for investigators to find “breadcrumbs” that lead to actionable evidence against extremists. What evidence they do find can be complex to analyze, making it difficult to find connections and links to other hostile players. Add the ability of these groups to disguise their true identities and online gathering points, and the actual threat levels of their stated plans as opposed to their claims, and tracking extremists online is no easy matter.
Unmasking, Tracking, and Prosecuting
With so many challenges facing investigators responsible for tracking extremists online, what tactics can they deploy to effectively unmask, track, and prosecute extremists?
Use technology-based force multipliers: To track extremists online and get a handle on their chatter, investigators need to probe the Surface Web and the Dark Web for a plethora of potential data that could be the breadcrumb that they need to start the process. This includes selected usernames and handles, email and website addresses, hashtags, subject lines, and topic discussions, dog whistles, disinformation, emojis and memes, and any other text or imagery associated with extremists who should be monitored by law enforcement for the public good. This can be done manually but will prove to consume a huge amount of time. Using technology to do the repetitive parts of this work in the background will speed up the process while freeing up law enforcement for other operational tasks. Once an investigator has this kind of information-gathering and analytical power on their side, they can deploy other tactics to improve their ability to deal with online extremists. These include:
Expand situational awareness. To effectively investigate extremists online, the responsible officer must become familiar with the websites, online tools, communications media, terminology, and imagery used by the extremists they are tracking. This is fundamentally no different than learning the culture of a motorcycle gang before going undercover. You have to have sufficient knowledge to intuitively connect the dots to understand what extremists are actually saying online, who they are saying it to, and how legally actionable their threats are.
Unmasking extremists: It is vital to unmask extremists, both online and in the community, so that law enforcement officers can know who they are actually dealing with and can be better placed to accurately assess the threat these people pose to society. Such information is vital both for assessing and deterring possible attacks and for mitigating actual attacks that do get through the net—because some will.
Spot and leverage mistakes: Be on the lookout for extremist slip-ups that can even reveal those who are off the grid because they do happen. In recent domestic events in the U.S., participants in various public demonstrations and riots who committed illegal acts uploaded images of themselves to various social platforms, making it possible to find and arrest them after the fact.
Even a small slip-up can make a difference. For instance, an extremist leader about to be evicted from one social platform may direct their followers to a new website and do so on the Surface Web. Similarly, an extremist may accidentally post some significant piece of personal information on the Surface Web such as selling items online and attaching a contact phone number that cross-references with their identity on the Dark Web. Adept investigators spot and capitalize on mistakes to unmask such extremists, track them and their associates and, whenever possible, arrest and prosecute them to the fullest extent of the law.
Keep an open mind: Extremists can be creative and novel in their attacks, and willing to acknowledge that fact in order to decipher and defuse their plans. The reason the 9/11 attackers succeeded was that conventional wisdom in 2001 did not foresee hijackers being willing to trade their lives in exchange for using seized airliners as guided missiles. Their novel actions defied what was known of organized hijacker behavior up to that point in time, and thus had not been pro-actively defended against.
Ongoing Concerns
The growth of online-enabled domestic extremism and the subsequent anti-social actions of its active members is not going to go away sometime soon. In fact, as long as there is Internet and broadband connectivity, it is not going to go away at all. Instead, online extremist activity is only likely to become more frequent, more widespread, and more violent in word and deed.
As such, law enforcement’s use of deep intelligence and other anti-extremist tools has become an ongoing requirement for agencies large and small. There’s no way to change this. All that can be done now is to marshal the very best law enforcement people and technology to combat extremists, by tracking their identities and actions online and – where possible – stopping their plans from coming to fruition.
Be warned: The detection and pursuit of extremists online is a long-term cat and mouse game. It’s a battle in which the advantage will go back and forth between law enforcement and extremists as one side learns new tricks and the other learns how to defeat them. By using the tools and tactics described above, law enforcement can and will win more of these battles, and save lives that otherwise would have been lost.
Johnmichael O’Hare is the sales and business development director of Cobwebs Technologies (www.cobwebs.com) He is the former commander of the Vice, Intelligence, and Narcotics Division for the Hartford (Connecticut) Police Department. Prior to that, he was the project developer for the City of Hartford’s Capital City Command Center (C4), a Real-Time Crime Center (RTCC) that reaches throughout Hartford County and beyond. C4 provided real-time and investigative support for local, state, and federal law enforcement partners utilizing multiple layers of forensic tools, coupled with data resources, and real-time intelligence. He can be reached atjohn.ohare@cobwebs.com